Red Team Operations that Simulate Real Adversaries — Not Checklists
We run controlled, intelligence-driven attack simulations to test whether your people, tooling, and response capability can withstand a real compromise across cloud, identity, applications, and AI systems.
WHAT IS RED TEAMING?
Red Teaming is a goal-based, intelligence-led security assessment designed to replicate how a real attacker would compromise your organisation. Rather than testing individual systems in isolation, Red Team operations assess the effectiveness of your detection capabilities, incident response processes, and security controls by attempting to achieve defined objectives—such as accessing sensitive data or compromising critical systems—without prior knowledge by defenders.
Why Red Teaming Matters
Our Red Team Approach
Our Red Team engagements follow a structured, intelligence-led methodology that mirrors how real adversaries plan, execute, and adapt attacks in the wild. Each phase builds on the previous one, allowing us to simulate realistic attack paths while maintaining strict operational control and authorisation.
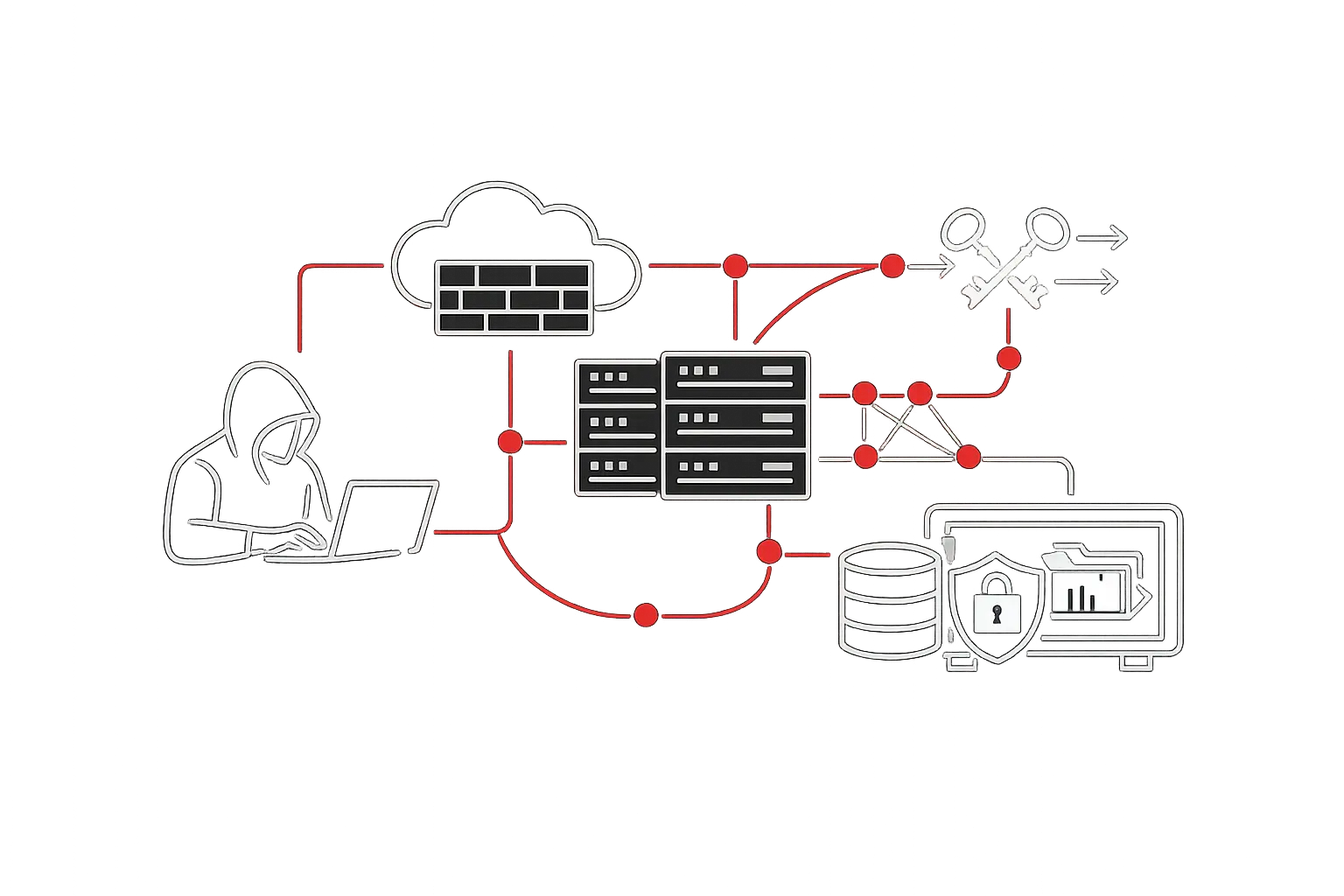
What We Test
Our Qualifications
Our Red Team capabilities are backed by continuous hands-on practice, industry-recognised certifications, and real-world offensive security experience.

Frameworks We Follow
We align our Red Team engagements with established security and adversary frameworks to emulate realistic attack patterns, assess control effectiveness, and provide outcomes that integrate seamlessly into existing security and governance programs.

Contact Us.
Our Locations:

Dubai UAE

Gampaha Sri Lanka